MikroTik RouterOS Hewlett-Packard Ubiquiti Networks MikroTik RouterOS, hack, computer Network, text png | PNGEgg
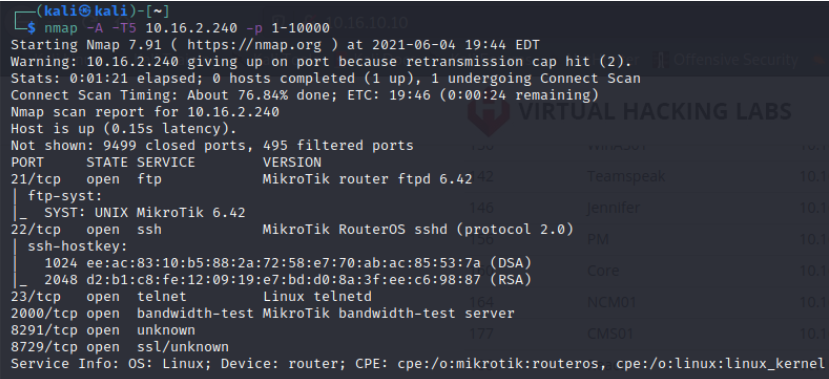
GitHub - 0x802/MikrotikSploit: MikrotikSploit is a script that searches for and exploits Mikrotik network vulnerabilities

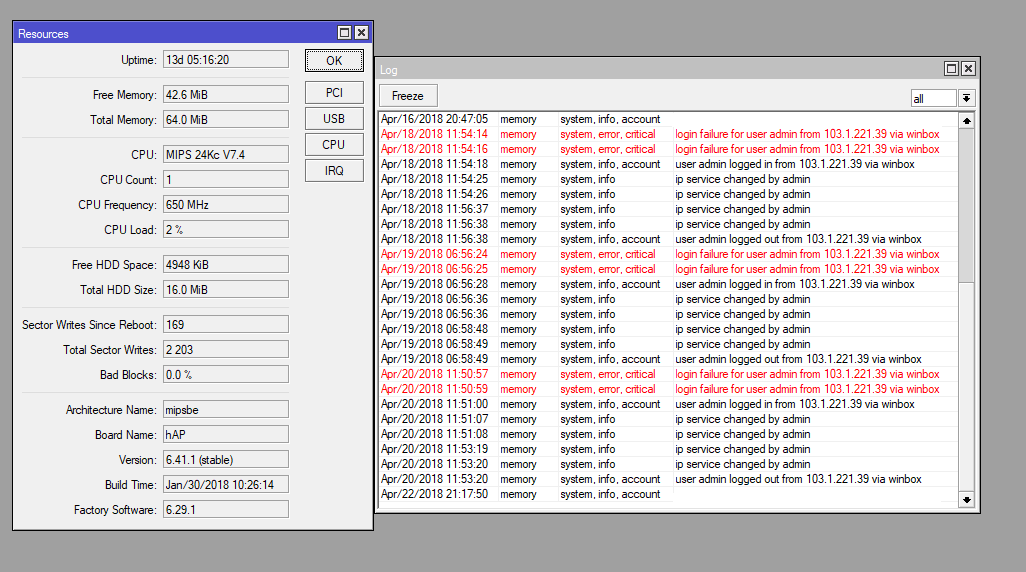
Password less Login to Remote Mikrotik & Linux | Syed Jahanzaib - Personal Blog to Share Knowledge !
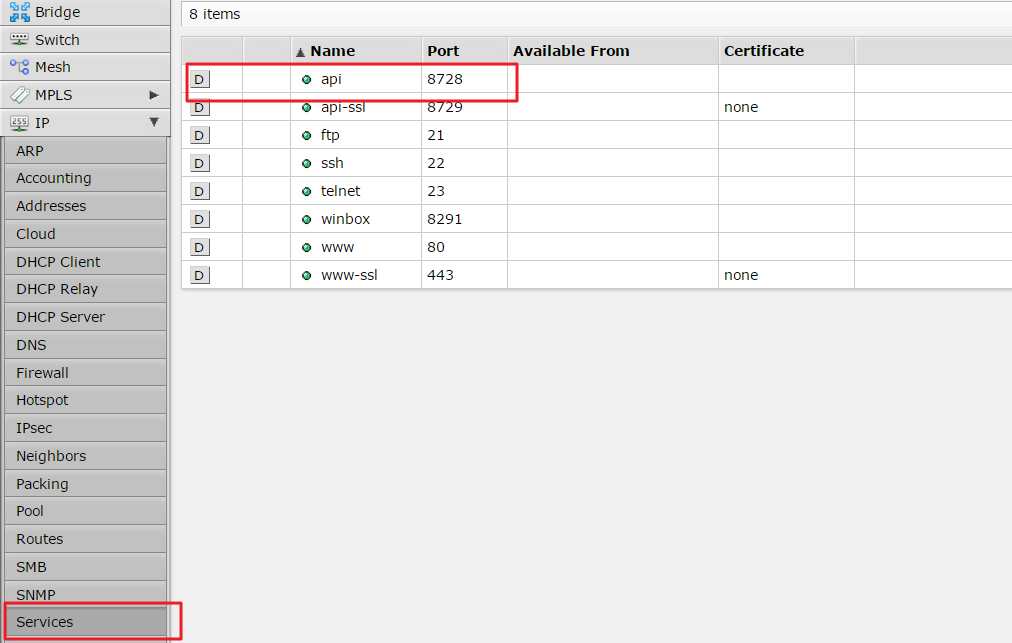
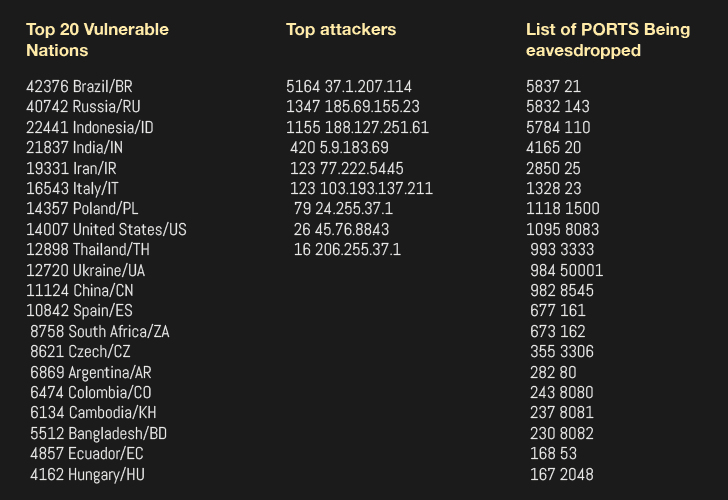

![New Tool] MKBrutus The Mikrotik RouterOS Bruteforce attacker tool v1.0.0 released – ToolsWatch.org New Tool] MKBrutus The Mikrotik RouterOS Bruteforce attacker tool v1.0.0 released – ToolsWatch.org](http://seguridadetica.files.wordpress.com/2013/11/mkbrutus_1.png)